Smart appliances are supposed to be the next big thing. Analysts predict that it’s a multi-billion dollar market. Why aren’t we there yet? Security. It’s a challenge for both manufacturers and users.
Once connected to the internet, IoT devices can do amazing things, but they also become vulnerable to hackers. There are two main reasons for this:
- Limited resources: Low-cost IoT toolkits simplify the task of developing new smart devices. The downside of these devices is that they’re often too underpowered to run security software or communicate securely.
- Lack of standards: Connected devices vary greatly in their security safeguards by manufacturer. If one device is hacked, it potentially compromises other devices on the same network.
Cloud-enabled security
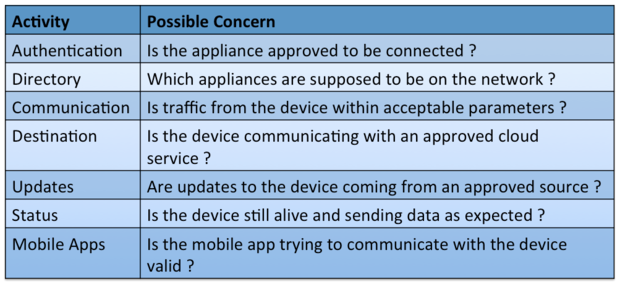
Chimefrom Innovation Labs by AVG (the antivirus and online security company) protects smart appliances by ensuring network traffic is authorized only to approved websites and mobile apps. Chime is installed on Wi-Fi routers and uses an online directory to stay current with new malware and hacking threats. It applies security techniques originally developed for enterprise security to also protect connected devices:
1. Two-factor authentication: Is that really you?
Chime creates a secure connection between the device and the owner’s authorized phone, tablet or computer. A hacker with stolen username and passwords is blocked from accessing the connected device unless the person also has physical access to a pre-authorized phone or PC by thistwo-factor authentication.
2. Blacklists and whitelists: In or out?
Chime develops a whitelistwith normal network behavior for each connected devices and a list of approved websites for updates. There’s also a blacklist of known viruses and IoT malware sites to block.
3. Heartbeat protocol: Are you still alive?
Users depend on their connected devices to alert them if something is wrong. What happens when a hacker intentionally disables an appliance and turns off sensor readings? Chime protects against this form of attack by checking the heartbeat of the device to make sure it’s still alive and working as planned.
 http://www.SkilledAnalysts.com
http://www.SkilledAnalysts.com “Many customers are unaware of the security threats when they install a smart appliance,” said Shaul Levi, who leads Innovation Labs. “We designed Chime to protect any smart appliance that communicates by Wi-Fi. It runs on the Wi-Fi router that’s already in the home and is continuously updated from an online database that includes AVG security updates and IoT services from partners.”
Unknown unknowns
“There are known knowns. There are things we know that we know. There are known unknowns. That is to say, there are things that we now know we don’t know. But there are also unknown unknowns. There are things we do not know we don’t know,” saidDonald Rumsfeld, the former U.S. Secretary of State, back in 2002.
He wasn’t talking about the IoT security, but hackers are definitely “unknown unknowns.” In such a situation, you’re safer with a lifeguard.
Resources:
This article is published as part of the IDG Contributor Network. Want to Join?
